 |
| Pentesting |
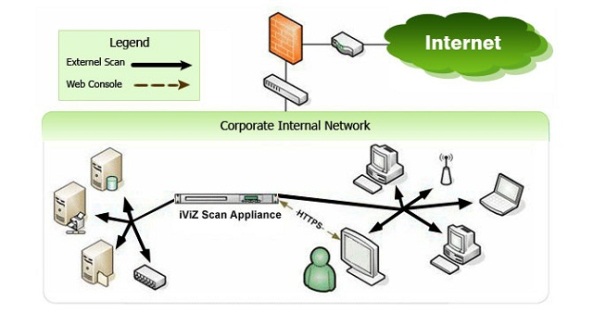
Introduction To Penetration Testing
In simple terms Penetration Testing means, testing your own system
for any Vulnerabilities or Loop holes to prevent it from the real
hackers.. The Penetration tester acts like an attacker to bypass the
securites to get access to the targeted system or network and report the
security breaches and vulnerabilities to the real owner of the
organisation’s.Pen Testing is that a tester use to gain unauthorised access to the organization’s network systems and compromise them. But pentester has limited in resources by time, skill, resources and access to equipment as per the agreement.
Also Check our previous Article to know more -> Penetrate your website before other do.
Actually pen testing reveals the potential consequences of a real attacker breaking into the organisation’s network. Thats why all the organisation’s conducting pen testing in a sequence interval of time to validate their security. Pentester is diffentiated from the attacker only by his intent and lack of malice.
Why Penetration Testing ?
Organisation’s has to identify the threats that they are facing in information assets.
For testing and validating their security protection and controls.
Organisations has to focus on high severity in vulnerabilites & application level security and management.
To prevent the upcoming exploits from the attacker.
Evaluating the efficiency of network security device such as firewall, routers & webservers.
For changing & upgrading theExisting infrastructure of software, hardware or network design.
 |
| Pentesting |
PenTesting Techniques PenTesting Tools
Vulnerability Scanners
Vulnerability Finding Techniques

No comments:
Post a Comment